Understanding Tekton Chains
Tekton Chains is a powerful security component within the Tekton ecosystem that helps secure your software supply chain by generating, signing, and storing provenance for artifacts built with Tekton Pipelines. This document provides an in-depth explanation of how Tekton Chains works and its key components.
TOC
Terminology
| Term | Description |
|---|---|
| SLSA | Supply-chain Levels for Software Artifacts - a security framework for software supply chain integrity |
| Signature | Cryptographic proof that verifies the authenticity and integrity of provenance data |
| Attestation | Authenticated metadata about software artifacts, following the in-toto attestation format |
| Verification | The process of checking the authenticity and integrity of attestation data |
| Type Hinting | Specially named results/params that help Tekton Chains understand inputs and outputs |
| Storage Backend | System where Tekton Chains stores provenance and signatures |
Attestation has multiple types of predicates.
| Predicate Type | Description |
|---|---|
| SLSA Provenance | Metadata that describes how an artifact was produced, including the build process, inputs, and environment |
| SBOM | A document that lists all the components of a software product and their relationships |
| Vulnerability Scan Results | A report that lists all the vulnerabilities found in a software product |
| Custom Metadata | Custom metadata about a software product |
Why Tekton Chains is Needed
The Software Supply Chain Security Challenge
In traditional software development and delivery pipelines, ensuring the integrity and security of artifacts throughout the supply chain presents significant challenges:
- Lack of Traceability: Without proper provenance information, it's difficult to verify where artifacts came from and how they were built
- Tampering Risks: Artifacts can be modified at various stages without detection
- Verification Difficulties: Consumers of artifacts have no reliable way to verify their authenticity
- Compliance Challenges: Organizations struggle to meet increasing regulatory requirements for software supply chain security
These challenges have led to high-profile supply chain attacks like SolarWinds, where malicious code was inserted into the build process, affecting thousands of organizations.
Tekton Chains' Solution
Tekton Chains addresses these challenges by:
- Automatic Provenance Generation: Capturing detailed metadata about the build process
- Cryptographic Signing: Ensuring the integrity and authenticity of provenance data
- Standardized Formats: Supporting industry-standard formats like SLSA provenance
- Flexible Storage: Providing multiple options for storing and retrieving provenance
- Integration with Existing Tools: Working with tools like Cosign, Syft, Trivy, Kyverno, Rekor, and cloud KMS services
- Cosign: A tool for signing, verifying, and managing signatures for container images
- Syft: A tool for generating SBOMs for container images
- Trivy: A tool for generating SBOMs and vulnerability scan results for container images, and scanning vulnerabilities
- Kyverno: Is a policy engine for Kubernetes that can be used to enforce security policies on container images
- Rekor: Is a public transparency log for signed artifacts
By implementing Tekton Chains, organizations can achieve higher levels of supply chain security and meet SLSA compliance requirements.
Advantages
- Automation: Automatically generates and signs provenance without manual intervention
- Standardization: Supports industry-standard formats like SLSA and in-toto
- Flexibility: Works with various signing mechanisms and storage backends
- Integration: Seamlessly integrates with the Tekton Pipelines ecosystem
- Transparency: Provides clear visibility into how artifacts were produced
- Compliance: Helps meet regulatory and industry requirements for supply chain security
Scenarios
Scenario 1: Image Signature Verification
A development team wants to ensure the integrity of their container images by implementing cryptographic signatures. By using Tekton Chains, they can automatically sign their built images and verify these signatures throughout their deployment process. This helps prevent unauthorized modifications and ensures that only trusted images are deployed.
Scenario 2: Build System Provenance Verification
An organization needs to verify the authenticity of their build process and ensure it follows their security requirements. By implementing Tekton Chains, they can generate SLSA Provenance for their container images, providing detailed information about how each image was built. This helps them maintain a secure and auditable build process.
Scenario 3: Source Code Repository Verification
A team wants to ensure that their container images are built from trusted source code repositories. By using Tekton Chains, they can automatically generate provenance that includes source code repository information and commit details. This helps them verify that images are built from the correct source code and specific commits.
Scenario 4: Vulnerability Scanning and Verification
A security team needs to ensure that their container images are free from known vulnerabilities before deployment. By implementing Tekton Chains with vulnerability scanning tools, they can automatically scan images for security issues and verify the scan results. This helps them maintain a secure container image registry and prevent vulnerable images from being deployed.
Scenario 5: Base Image and SBOM Verification
An organization wants to maintain a complete inventory of their container image components and ensure they're using trusted base images. By using Tekton Chains with SBOM generation tools, they can automatically generate and verify software bill of materials for their images. This helps them track dependencies and ensure compliance with their security policies.
Scenario 6: License Compliance Verification
A legal team needs to ensure that all software components in their container images comply with their license requirements. By implementing Tekton Chains with SBOM verification, they can automatically check the licenses of all components in their images. This helps them maintain compliance with software licensing requirements and avoid potential legal issues.
Scenario 7: Keyless Signing Verification
A development team wants to implement a zero-trust signing approach without managing signing keys. By using Tekton Chains with keyless signing capabilities, they can automatically sign their artifacts using ephemeral keys and transparency logs. This helps eliminate key management overhead while maintaining strong security guarantees.
Constraints and Limitations
- Kubernetes Dependency: Requires a Kubernetes cluster with Tekton Pipelines installed
- Configuration Complexity: Proper type hinting configuration is required for accurate provenance
- Key Management: Secure management of signing keys is essential
- Storage Requirements: Additional storage is needed for provenance and signatures
- Performance Impact: Signing and storing provenance adds some overhead to the build process
Principles
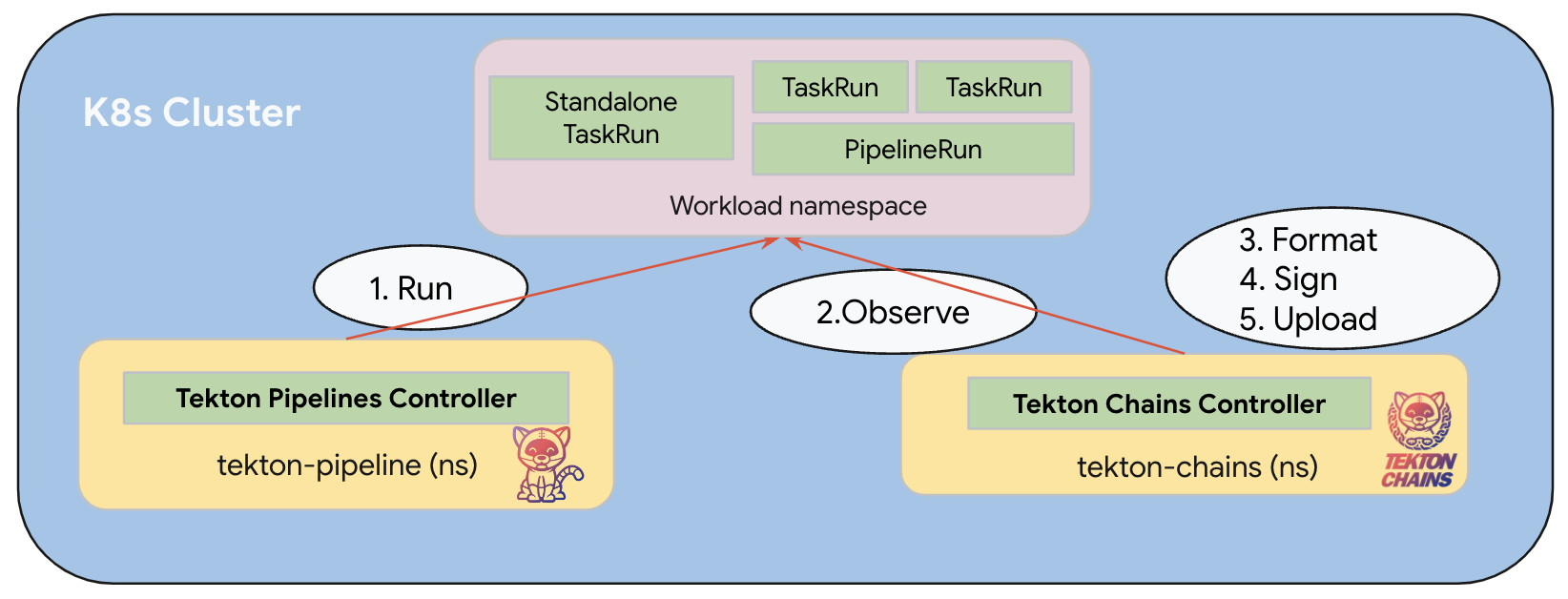
How Tekton Chains Works
Tekton Chains operates through a controller that observes TaskRun and PipelineRun resources in a Kubernetes cluster. The workflow follows these steps:
- Observation: The controller watches for completed TaskRuns and PipelineRuns
- Snapshot: When a run completes, Chains takes a snapshot of its state
- Formatting: Chains generates provenance in the configured format (e.g., SLSA)
- Signing: The provenance is cryptographically signed using the configured method
- Storage: Both the provenance and signature are stored in the configured backends
Provenance Generation
Tekton Chains uses type hinting to understand the inputs and outputs of a build process. This information is then used to generate provenance in the specified format:
- Input Collection: Chains identifies input artifacts through type hints
- Build Process Capture: Details about the build environment and steps are recorded
- Output Identification: Output artifacts are identified through type hints
- Provenance Assembly: All information is assembled into a standardized format
Signing Process
Tekton Chains supports multiple signing methods to accommodate different security requirements:
- Key Retrieval: The signing key is retrieved from the configured source
- Payload Preparation: The provenance data is prepared for signing
- Signature Generation: A cryptographic signature is generated
- Verification Data: Additional data needed for verification is included
Configuration Examples
Basic SLSA v1.0 Configuration
Type Hinting
More details about type hinting can be found in the Tekton Chains Type Hinting documentation.
Type Hinting is a special mechanism in Tekton Chains that helps Chains understand input artifacts and output artifacts in PipelineRun/TaskRun through specific naming conventions.
Purpose
- Helps Chains correctly identify and record input and output artifacts in the build process
- Generates accurate SLSA Provenance attestations
- Ensures traceability and integrity of the build process
There are several ways to specify input and output artifacts:
1. CHAINS-GIT_URL and CHAINS-GIT_COMMIT combination
- Special type hints for Git repository information
- Used to track source code repository details
- Helps in provenance generation for source code
Example TaskRun
2. *ARTIFACT_INPUTS
Note:
*indicates any expression
- Used to specify input artifacts that influenced the build process
- Helps track dependencies and source materials
Example TaskRun
3. *IMAGE_URL and *IMAGE_DIGEST combination
Example TaskRun
4. IMAGES
- Can specify multiple images, separated by commas or newlines
- Each image must include the complete digest
Example TaskRun
5. *ARTIFACT_URI / *ARTIFACT_DIGEST combination
- Similar to IMAGE_URL/IMAGE_DIGEST but with different naming convention
- Used for specifying artifact location and its digest
6. *ARTIFACT_OUTPUTS
- Uses object type results
- Must include uri and digest fields
Example TaskRun
Important Parameters
Storage Configuration
Storage backends determine where provenance and signatures are stored. This is crucial for ensuring that provenance is accessible when needed for verification.
Use Cases
- Tekton Storage: Useful for debugging and internal verification
- OCI Storage: Ideal for storing provenance alongside container images
- GCS/DocDB Storage: Suitable for centralized storage and management
Configuration Example
Signing Configuration
The signing configuration determines how provenance is cryptographically signed, which is essential for verifying its authenticity.
Use Cases
- x509: Standard certificate-based signing
- KMS: Cloud-based key management for enhanced security
- Keyless: Zero-trust signing with ephemeral keys