Alauda Container Security Plugin Installation
This guide provides step-by-step instructions for installing the Alauda Container Security plugin.
TOC
Installation Requirements
- Architecture:
amd64 - Kernel version:
>=5.8 - Resource requirements:
- CPU:
>=4 - Memory:
>=8GB
- CPU:
- PostgreSQL:
>=13 - TLS Certificate
Central Service Plugin Installation
Pre-installation Steps
-
Create the stackrox namespace:
-
Create the central-db-password secret:
Store the password in thepassworddata item. -
Enable Ingress and configure domain certificate:
Create a TLS secret with your certificate and key. -
Create additional CA secret :
Install via UI
- In Platform Management, go to Marketplace → Cluster Plugins.
- Click the Install button next to the Central Service for StackRox plugin.
- Fill in the storage class and configuration parameters as prompted.
| Parameters | Description |
|---|---|
| Central Database Connection String | The connection string for the central database.For example: host=acid-business-1.proj01-postgres.svc port=5432 user=postgres sslmode=require |
| Host | Specify a custom hostname for the central ingress. Specify a "central-ingress-tls" ts type secret in stackrox namespace that contains tls.crt, tls.key. |
Install via YAML
Apply the following YAML to your target cluster:
Access Central Console
- Address:
https://example.com(The address of the central ingress host) - Initial account:
admin/07Apples@
Cluster Service Plugin Installation
Generate Cluster Access Certificate
-
In Platform Configuration, go to Platform Configuration → Integrations.
-
Click the button of Authentication Tokens --> Cluster Init Bundle

-
Click Create bundle.
-
Enter the name of the access cluster and download the generated file (e.g.,
business-1-Operator-secrets-cluster-init-bundle.yaml).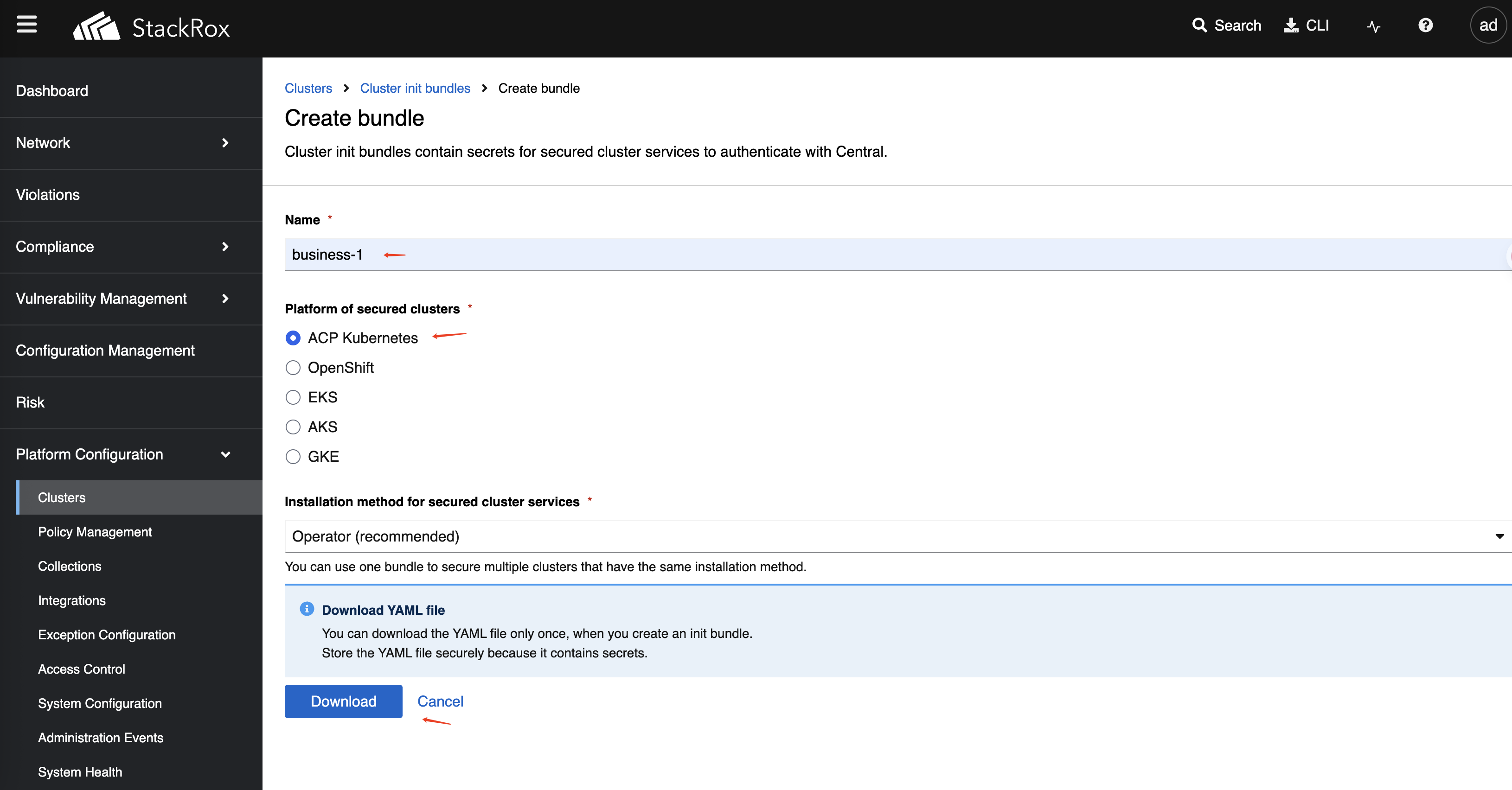
Cluster Pre-installation Steps
-
Create the stackrox namespace:
-
Apply the cluster init bundle secret:
3.If the central domain uses an untrusted certificate, you need to create the additional-ca-sensor secret. Configure Ingress domain certificate :
Cluster Install via UI
- In Platform Management, go to Marketplace → Cluster Plugins.
- Click the Install button next to the Cluster Service for StackRox plugin.
- Fill in the storage class and configuration parameters as prompted.
Note: The Central service address is the access address, e.g.,
wss://example.com:443.
Cluster Install via YAML
Apply the following YAML to your target cluster:
Plugin Uninstallation
After uninstalling the plugin, manually clean up the following secret resources in the stackrox namespace if they remain:
| Secret Name Pattern | Description |
|---|---|
| central-* | Central related secrets |
| scanner-* | Scanner related secrets |
| sensor-tls | Sensor TLS secret |
| service-ca | Service CA secret |
| admission-control-tls | Admission control TLS |
| collector-tls | Collector TLS secret |
| stackrox-generated-once | One-time generated secret |